Tails 6.11
Critical security fixes
The vulnerabilities described below were identified during an external security audit by Radically Open Security and disclosed responsibly to our team. We are not aware of these attacks being used against Tails users until now.
These vulnerabilities can only be exploited by a powerful attacker who has already exploited another vulnerability to take control of an application in Tails.
If you want to be extra careful and used Tails a lot since January 9 without upgrading, we recommend that you do a manual upgrade instead of an automatic upgrade.
Prevent an attacker from installing malicious software permanently. ( #20701)
In Tails 6.10 or earlier, an attacker who has already taken control of an application in Tails could then exploit a vulnerability in Tails Upgrader to install a malicious upgrade and permanently take control of your Tails.
Doing a manual upgrade would erase such malicious software.
Prevent an attacker from monitoring online activity. ( #20709 and #20702)
In Tails 6.10 or earlier, an attacker who has already taken control of an application in Tails could then exploit vulnerabilities in other applications that might lead to deanonymization or the monitoring of browsing activity:
- In Onion Circuits, to get information about Tor circuits and close them.
- In Unsafe Browser, to connect to the Internet without going through Tor.
- In Tor Browser, to monitor your browsing activity.
- In Tor Connection, to reconfigure or block your connection to the Tor network.
Prevent an attacker from changing the Persistent Storage settings. ( #20710)
New features
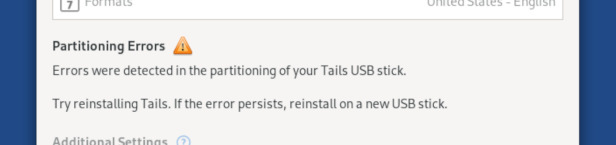
Detection of partitioning errors
Sometimes, the partitions on a Tails USB stick get corrupted. This creates errors with the Persistent Storage or during upgrades. Partitions can get corrupted because of broken or counterfeit hardware, software errors, or physically removing the USB stick while Tails is running.
Tails now warns about such partitioning errors earlier. For example, if partitioning errors are detected when there is no Persistent Storage, Tails recommends that you reinstall or use a new USB stick.
Changes and updates
Update Tor Browser to 14.0.4.
Update Thunderbird to 128.5.0esr.
Remove support for hardware wallets in Electrum. Trezor wallets stopped working in Debian 12 (Bookworm), and so in Tails 6.0 or later.
Disable GNOME Text Editor from reopening on the last file. ( #20704)
Add a link to the Tor Connection assistant from the menu of the Tor status icon on the desktop.
Make it easier for our team to find useful information in WhisperBack reports.
For more details, read our changelog.
Tails 6.11 has been released, incorporating essential security fixes that address vulnerabilities. These solutions effectively mitigate the risk of attackers installing malicious software permanently, monitoring online activities, and altering Persistent Storage settings. Manual upgrades can eliminate malicious software and safeguard against unauthorized access to Tails applications. Furthermore, Tails now alerts users to partitioning errors, thereby preventing them from reinstalling or utilizing a new USB stick.